Monitoring user’s activity with auth logs
CRMs are great for collaboration. They allow your employees to access information they need, coordinate their efforts, communicate, share notes, and work towards common goals more effectively. But as more people are using the software, sometimes you may need to know what each team member is doing in the system. Who and when is logging in? Who is updating records? And who has accidentally deleted that important contact?
There’s a surprisingly simple method to get answers to all these questions: checking auth logs. They record user logins (including time and IP address) and provide a chronological history of actions performed on specific records. Let’s find out how you can access them.
To track the authorized users, their IP Address, and time when they logged in, just go to Administration > Auth Log.
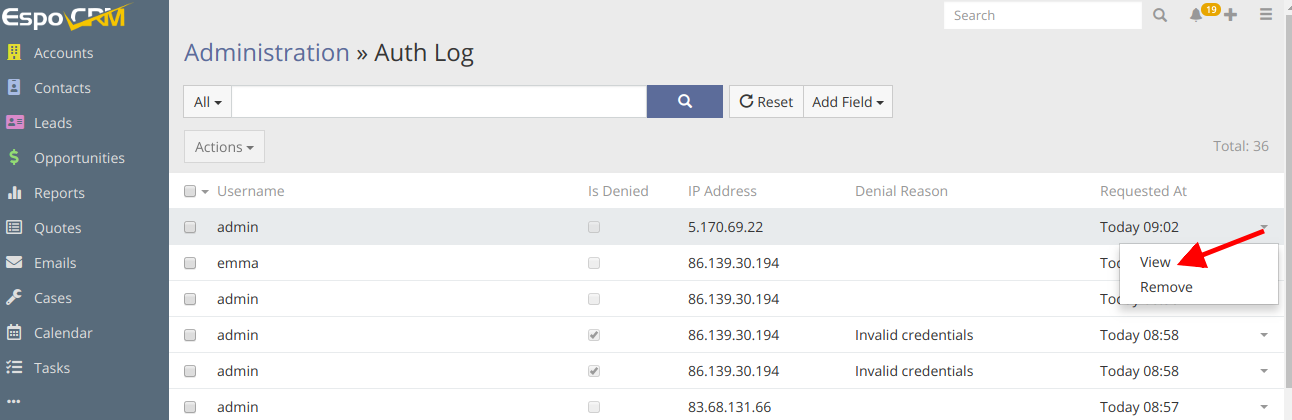
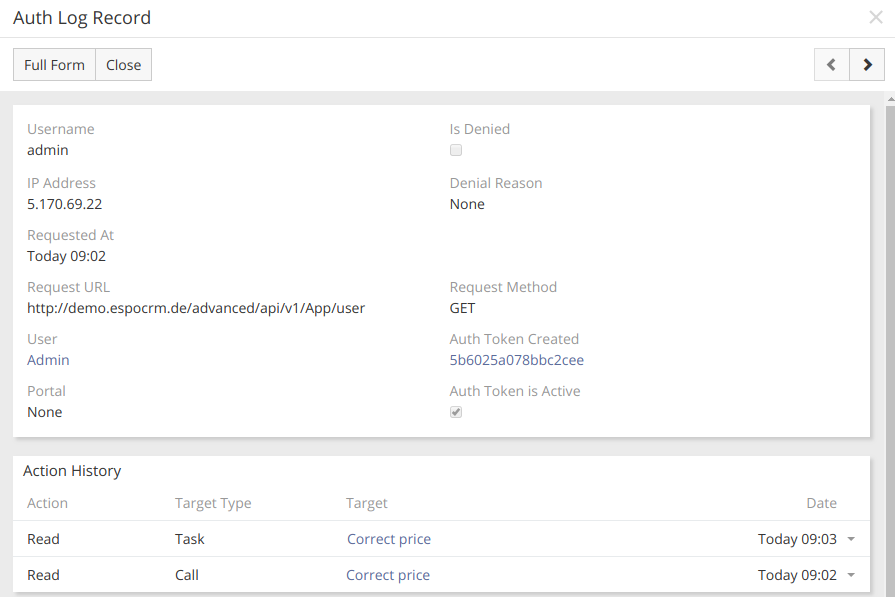
With a few clicks, you will be able to find here detailed information about logged in users, their actions and even remove a log record if needed. You can also track the attempts of unauthorized access and the IP addresses of those who tried to do it, which in turn will help you to ensure your data security.
Hope the information was useful for you! Thanks for paying attention!
